Want
to stay up to date?
Discover our free PC magazine PC newsflash now
Latest update: 19-8-2003: W32/Nachi.A virus
URGENT ALERT - MSblaster.exe
virus
There is a new trojan virus around
spreading around quite fast. If your Windows
XP is closing down all the time without a reason you can have this virus
on your pc.
When the virus is active and you go
online you will get this message:
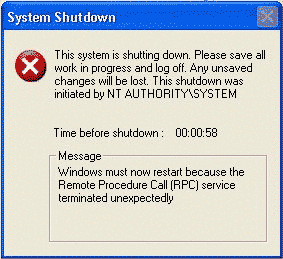
To check press control+alt+del button to
see the tasks operating on your
machine, if msblaster.exe is active you are infected.
Also check Windows/System32 directory for a file called msblaster.exe
W32.Blaster.Worm is a worm that exploits
the DCOM RPC vulnerability (described in Microsoft
Security Bulletin MS03-026) using TCP port 135. This worm attempts to
download the msblast.exe file to the %WinDir%\system32 directory and then execute it. The
worm has no mass-mailing functionality.
The worm also attempts to perform a Denial of Service (DoS) on the Microsoft Windows
Update Web server (www.windowsupdate.com). This is an attempt to prevent you from applying
a patch on your computer against the DCOM RPC vulnerability.
To remove the virus download this tool now
More info on this tool here
To be sure your windows is clean check
this:
- Reboot your system
- Press ctrl+alt+del button to see tasks which are active (look for msblaster)
- Check windows / system32 directory for msblaster.exe file
- Start windows/regedit.exe utilty and look for registry key:
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\Run
See if it contains: windows auto
update"="msblast.exe"
if so remove that entry and close regedit